1. Introduction
While not purpose-built for insider threat, Microsoft Purview provides essential enforcement capabilities that strengthen internal security posture across compliance, legal, and investigative functions. Through features like data classification, policy-driven alerts, communication monitoring, and audit logging, Purview equips organizations with the operational controls needed to manage sensitive information and respond to behavioral risk, laying the groundwork for defensible access, scoped investigations, and principled enforcement in complex environments.
This article explores how Purview’s role-based permission model supports Insider Risk Management (IRM), including an overview of built-in role groups, custom configurations, and integration with Microsoft Entra Privileged Identity Management (PIM) for just-in-time access. We also examine the operational implications of these controls and how they contribute to accountable, auditable, and risk-aligned access strategies.
2. Purview Role Groups
Purview role groups are permission sets composed of roles, used within the Microsoft Purview compliance portal to manage access to compliance, data lifecycle, and investigative features, such as eDiscovery, Insider Risk Management, and Data Classification. Unlike Entra ID roles, which are tenant-wide and managed centrally through Microsoft Entra ID, Purview roles are assigned via role groups in the Purview portal and follow a separate permissions model tailored to compliance use cases. These roles are designed for investigators, compliance officers, legal teams, and HR personnel, providing scoped access to sensitive compliance data and tools.
3. Insider Risk Management Permissions
There are six built-in role groups for Insider Risk Management features within Purview compliance. Microsoft provides a useful table to help understand what actions each IRM role group can take:
Actions | Insider Risk Management (IRM) | IRM Admins | IRM Analysts | IRM Investigators | IRM Auditors | IRM Approvers |
|---|---|---|---|---|---|---|
Access & investigate alerts | Yes | No | Yes | Yes | No | No |
Access & investigate cases | Yes | No | Yes | Yes | No | No |
Access & view forensic evidence captures | Yes | No | No | Yes | No | No |
Access & view the Content Explorer | Yes | No | No | Yes | No | No |
Access analytics insights | Yes | Yes | Yes | No | No | No |
Approve forensic evidence capturing requests | Yes | No | No | No | No | Yes |
Configure Adaptive Protection | Yes | Yes | No | No | No | No |
Configure notice templates | Yes | No | Yes | Yes | No | No |
Configure policies and settings | Yes | Yes | No | No | No | No |
Create forensic evidence capturing request | Yes | Yes | No | No | No | No |
View & export audit logs | Yes | No | No | No | Yes | No |
View Adaptive Protection users tab | Yes | No | Yes | Yes | No | No |
View alert and case reports | Yes | Yes | Yes | Yes | No | No |
View data risk graphs for alerts | Yes | No | Yes | Yes | No | No |
4. Custom Role Groups
While the in-built role groups in Purview are generally suitable for most use cases out of the box, it is possible to create custom role groups and define the specific permissions required.
Within the Purview portal, go to Settings, Roles and scope, Role groups, and select "Create role group":
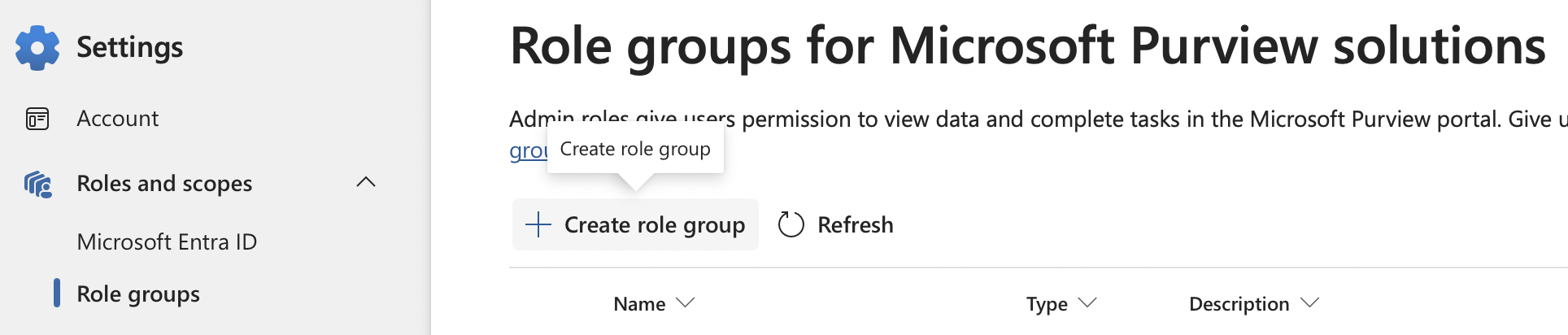
Assign the role group an appropriate name and description. In this example, a new role group is being created to take the base permission set for Insider Risk Management Analysts, and also providing the ability to access and view the content explorer.
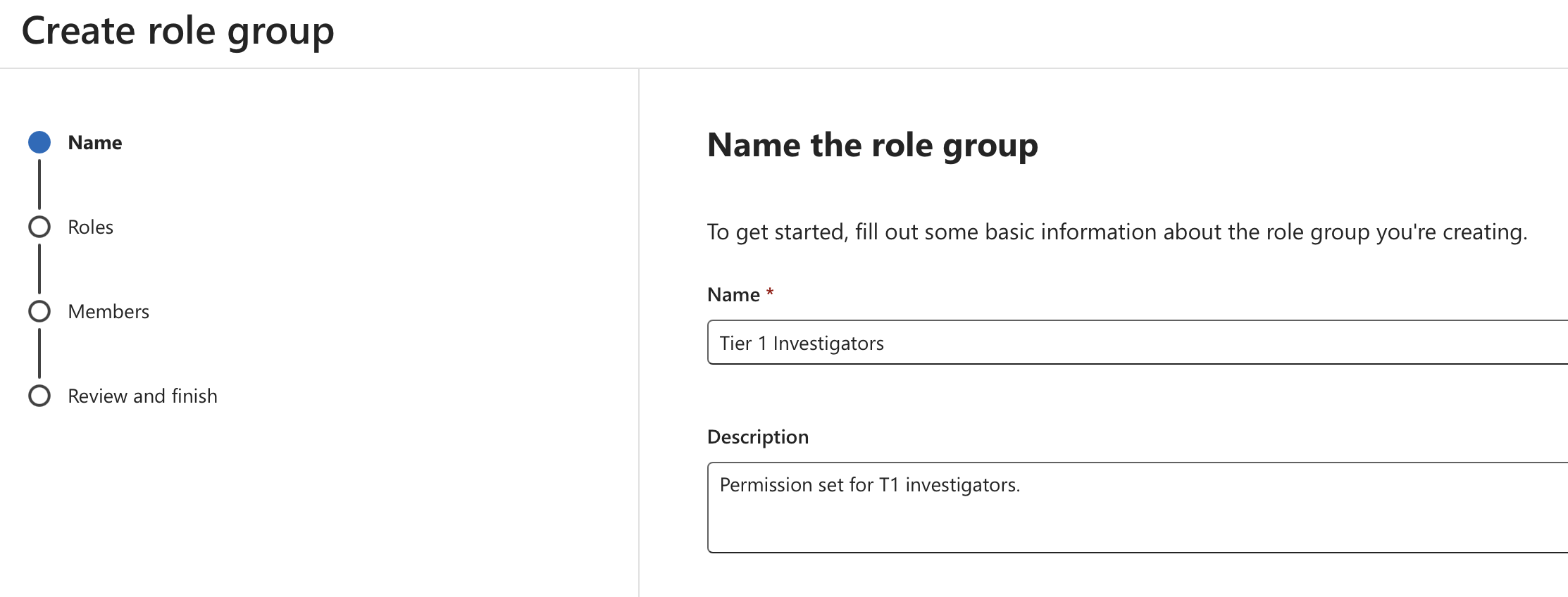
Next, roles can be selected to build out the permissions that members of the role group have. As per the example, both "Insider Risk Management Analysis" and "Purview Content Analyst" have been added.
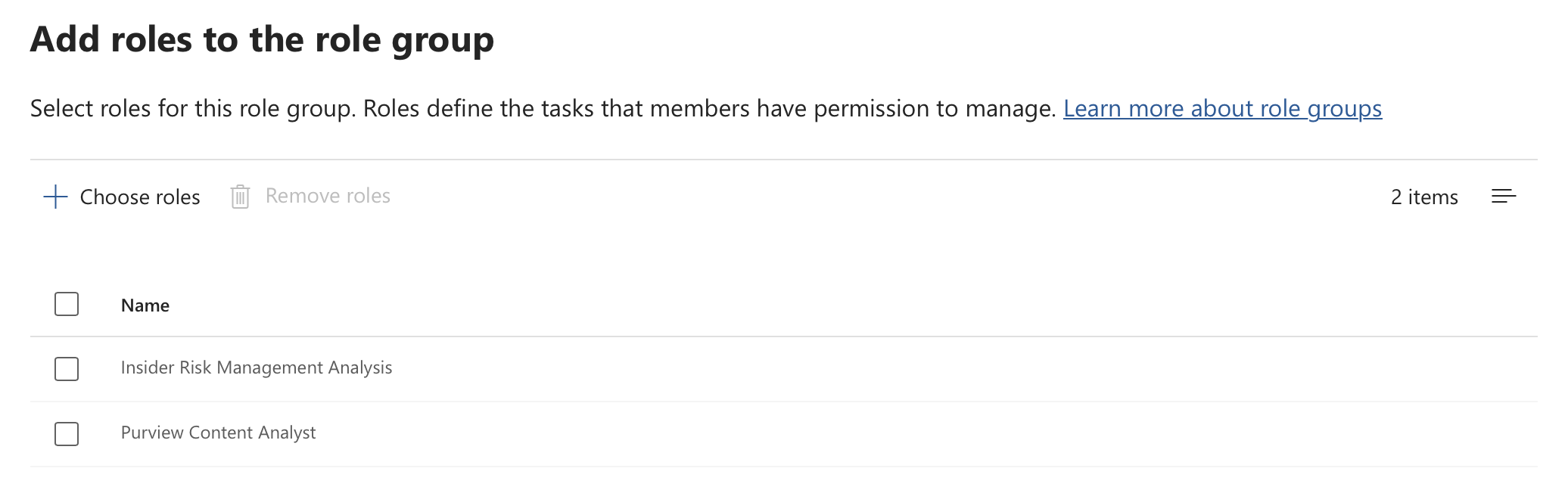
Members, Entra ID users or groups, can be added to the role group and will inherit the associated permissions.
5. Role Membership Considerations and Just-in-Time Access
Access to Purview groups can be granted to Entra ID users or groups. This presents several options for handling Purview permissions, and even gating them behind an auditable privileged identity management process, ensuring that access is only granted when required.
5.1. Always On Access, Individual Users and Groups
Purview role groups can be permanently attached to user accounts by selecting the role group (Purview compliance > Settings > Roles and scopes > Role groups) [Link] and adding the user from the "Choose users" tab:
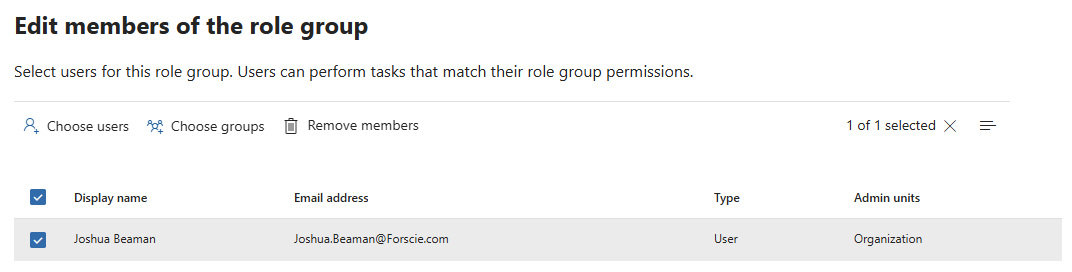
Alternatively, Entra groups can be added from the "Choose groups" tab:
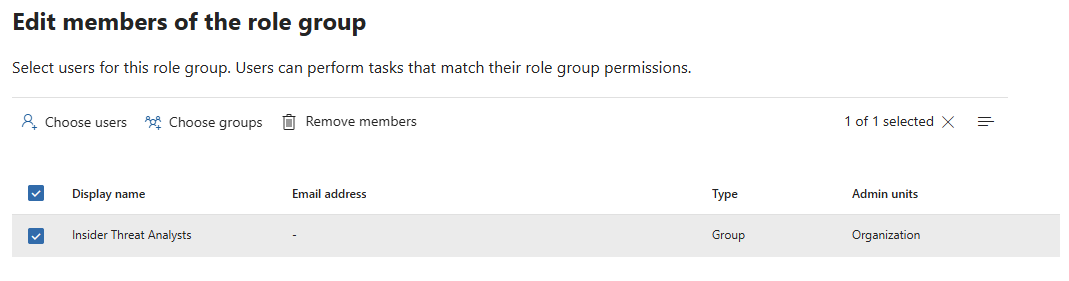
5.2. Just-in-Time Access via Azure PIM
Microsoft Entra ID Privileged Identity Management (PIM) is a control mechanism that enables time-limited, auditable elevation to privileged roles or group memberships. It is designed to reduce standing access, enforce least privilege, and ensure that sensitive permissions are only granted when operationally required.
Just-in-Time (JIT) access shifts the access model from proactive entitlement to on-demand elevation, dramatically reducing the attack surface and helping organizations maintain a defensible enforcement position. In the context of insider risk, JIT reduces the window in which high-trust roles can be misused, while preserving operational flexibility for legitimate investigations or policy enforcement actions.
5.2.1. Group Configuration
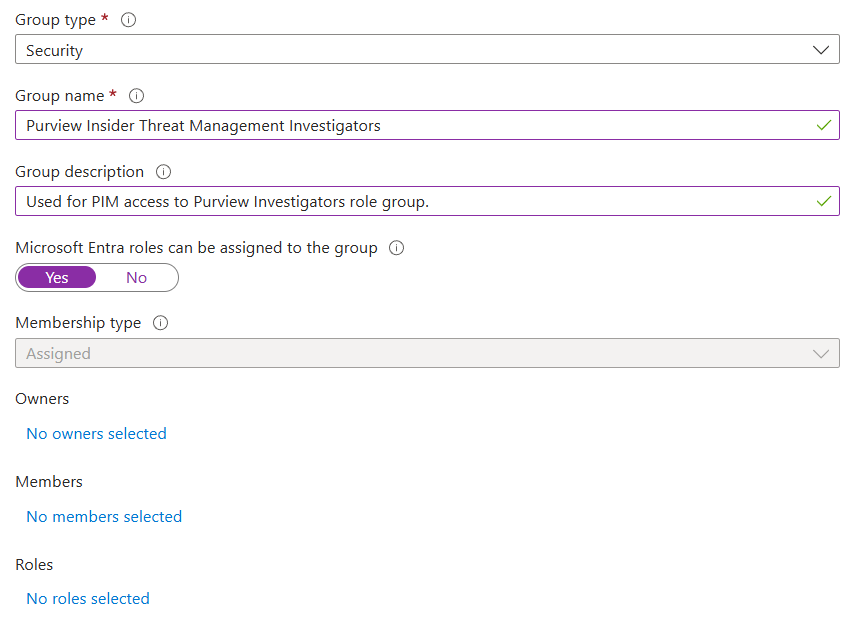
To time-gate access to the Insider Risk Management Investigators role group within Purview, an associated Entra group must be created (Entra ID > Manage > Groups) [Link]. It's important that "Microsoft Entra roles can be assigned to the group" is toggled to "Yes", so individuals can activate assignment to this resource through Azure PIM.
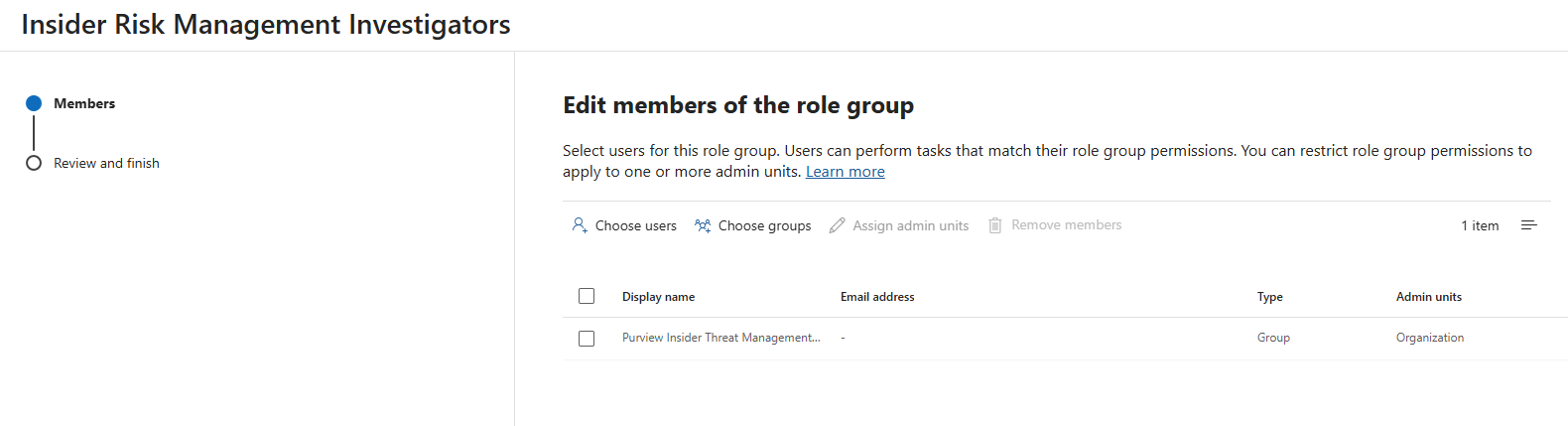
Now that the group has been created, we need to include it as a member of the Purview Insider Risk Management Investigators role group from within the Purview compliance portal (Purview compliance > Settings > Roles and scopes > Role groups > Insider Risk Management Investigators) [Link]:
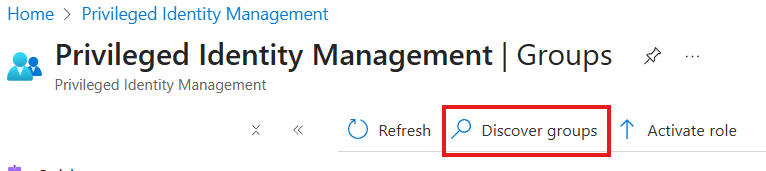
In the PIM portal, select "Groups" then "Discover groups" (PIM > Manage > Groups) [Link]:
Search for and select the created Entra group:
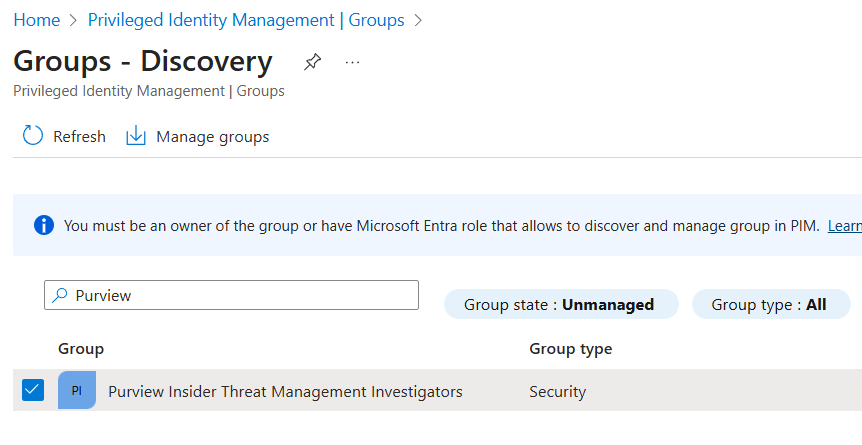
Select any appropriate users who can use PIM to gain membership in this group:
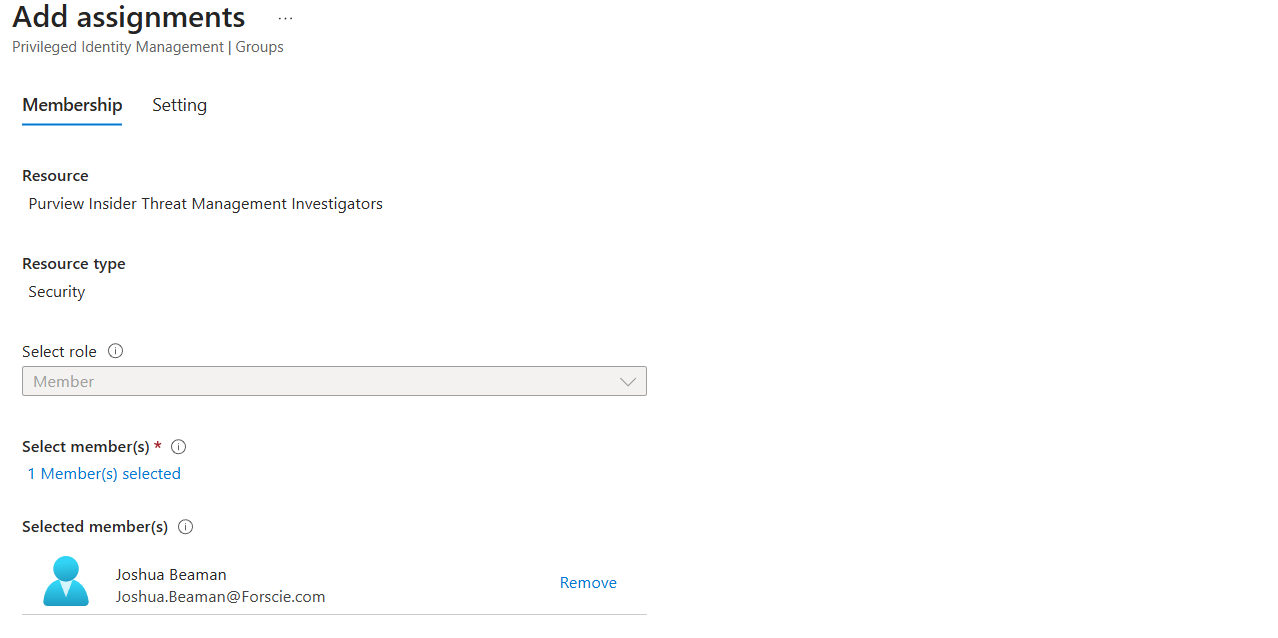
On the next page, ensure "Assignment type" is set to "Eligible" so this membership is not permanent, and must be activated. The assignment start and end dates can be adjusted, but by default are set to the maximum eligibility timeframe of 1 year. It's important to note that because of this, users will need to be assigned to this group again in a year to maintain eligibility.
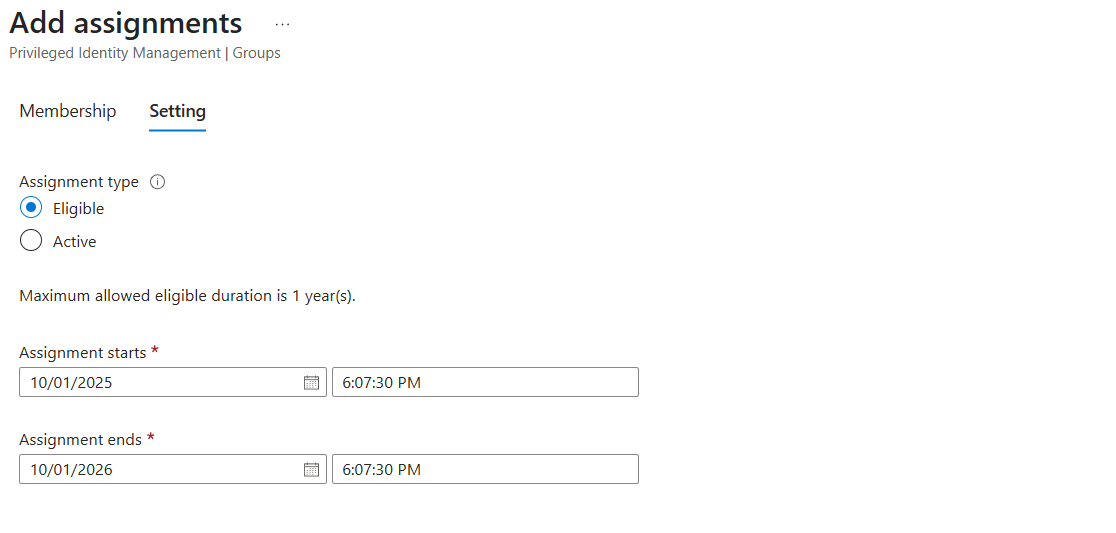
5.2.2. Additional Settings
There are additional settings that can be configured, such as how a user activates the assignment, implementing an approval process, and more granular notifications to provide oversight. Select the relevant group, and under the Manage section on the left navigation menu, select Settings. While it is possible to edit settings for both Owners and Members of the group, as users are only eligible to activate the member role, this row should be clicked.
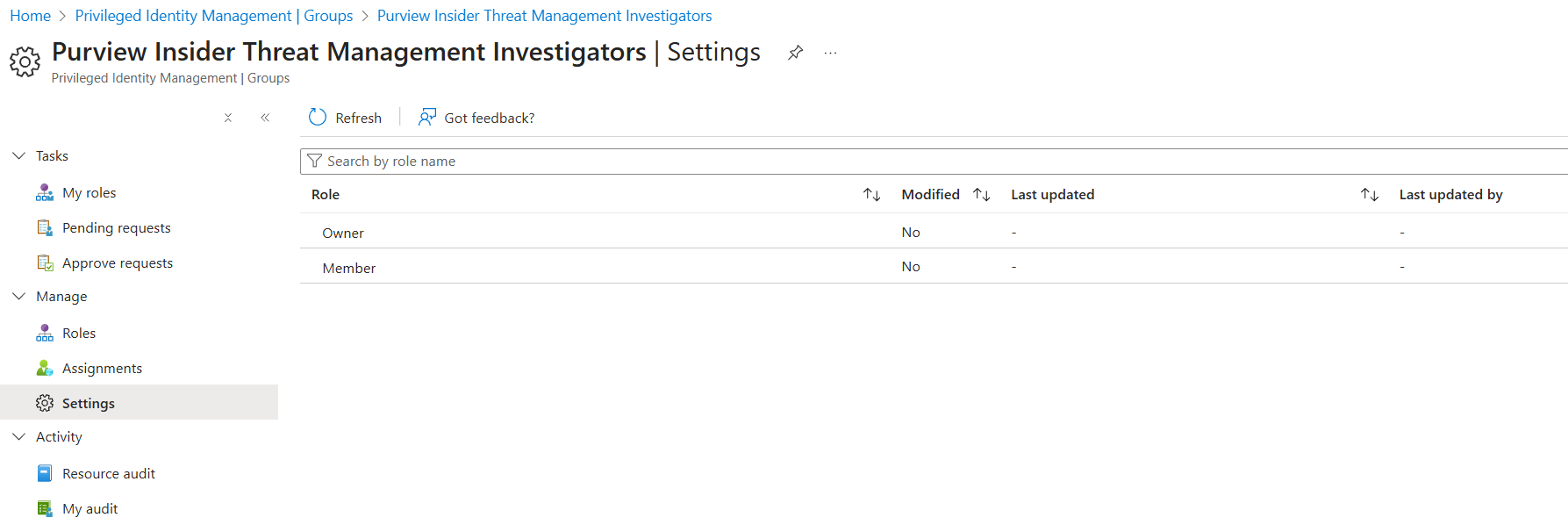
The most notable setting here is the checkbox for "Require approval to activate". If set to true, one or more users or groups must be selected that will manually approve activation requests. While this introduces significant overhead to the elevation process, this oversight may be appropriate in some environments. For redundancy, the best approach may be to use an Entra ID group for users who can approve these requests to prevent a single point of failure if only one individual can approve activations.
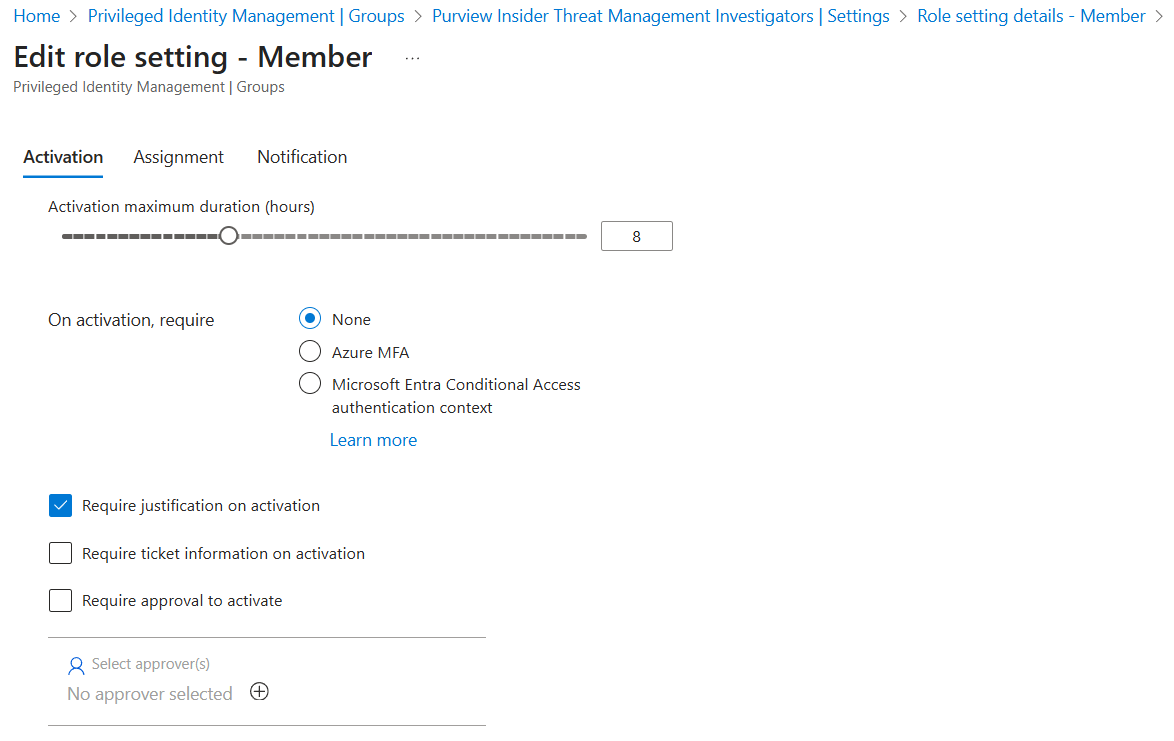
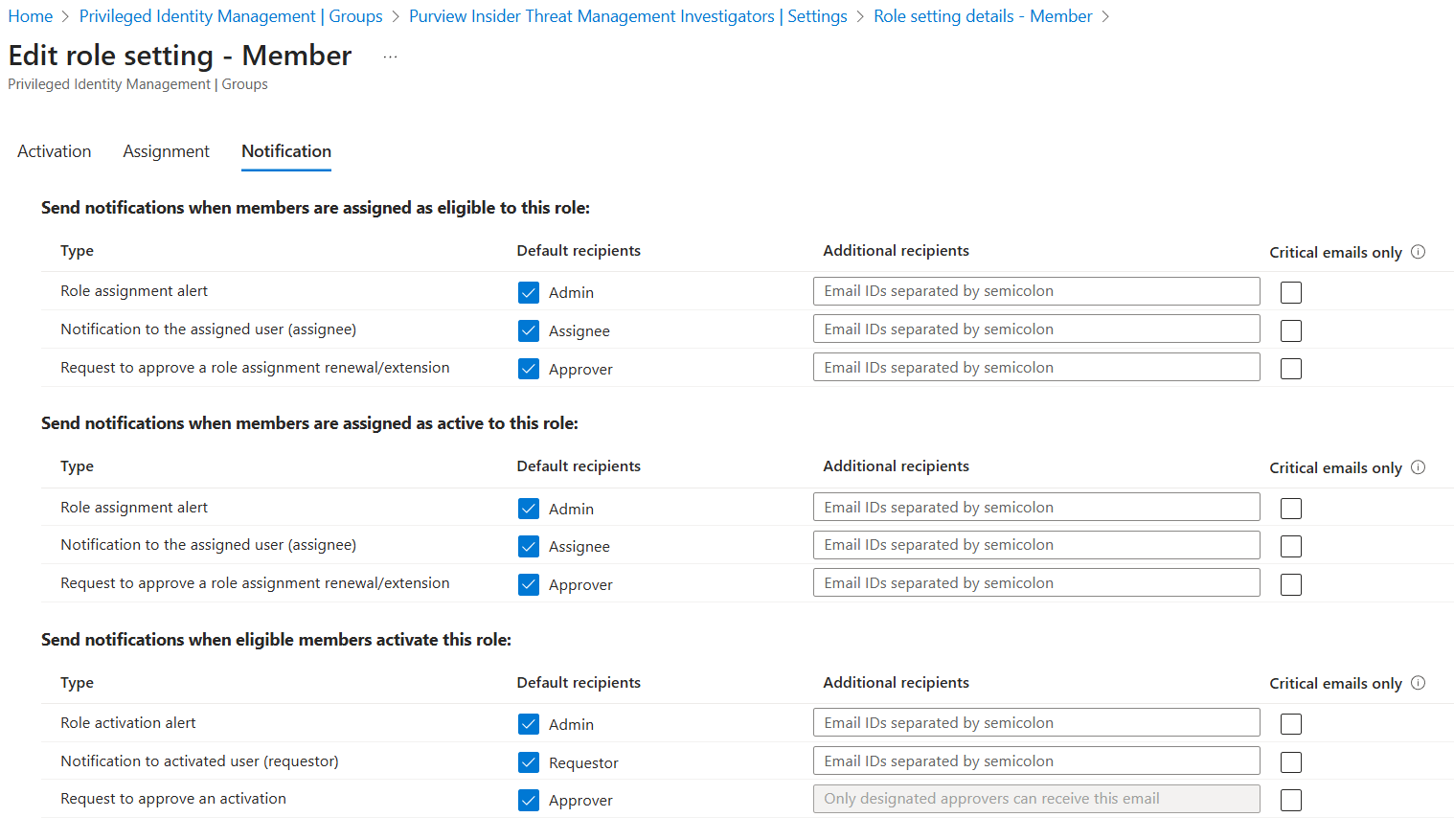
By default, all notifications have default recipients - additional recipients can be configured. Suppose approval for activations is not enabled, to enable immediate oversight. In that case, it may be appropriate to add the email address of the individual(s) responsible for the Insider Risk Program as an additional recipient.
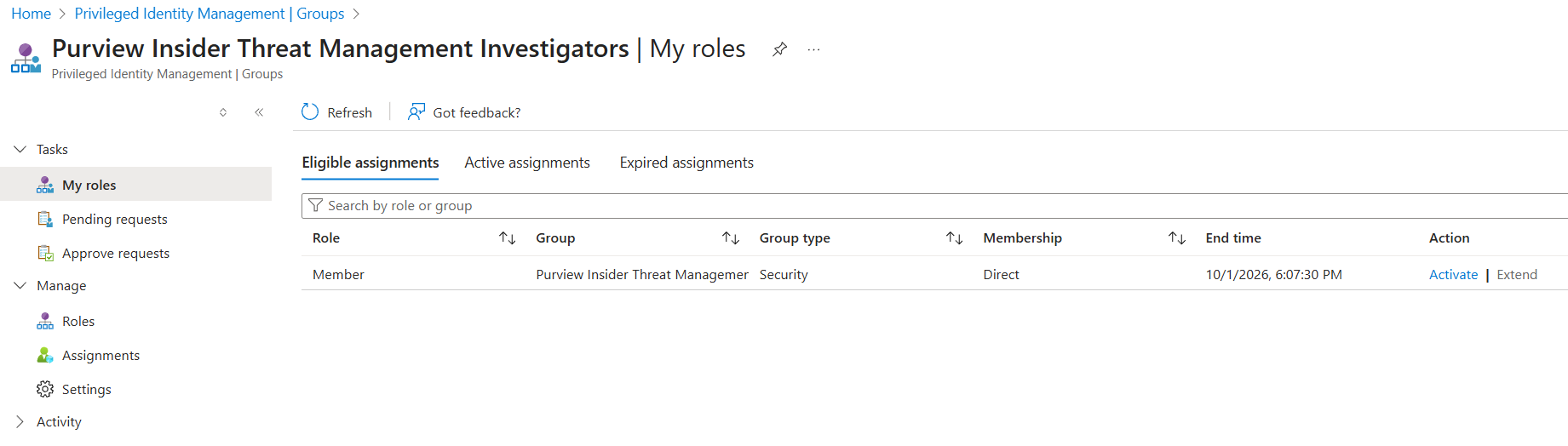
5.2.3. Assignment Activation
When a user needs to elevate to the Investigators Entra group to obtain Insider Risk Management Investigators permissions, they can navigate to the PIM portal, and they will see the Entra group as an eligible assignment. Clicking "Activate" will begin the elevation flow.
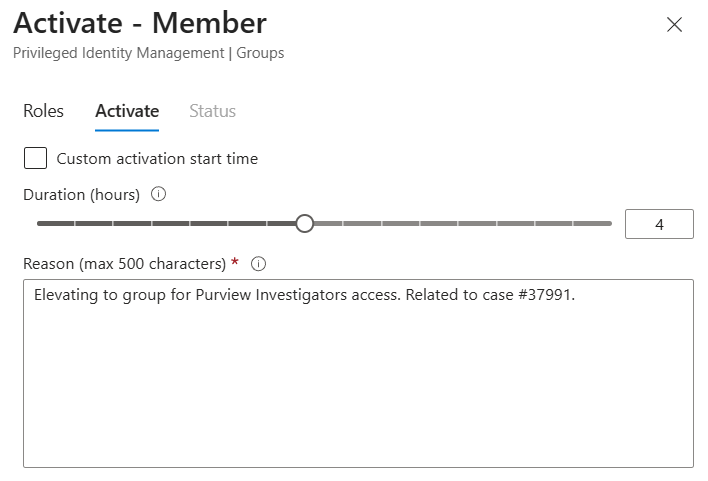
A duration is set (default 8 hour maximum), and the user must provide a reason for the elevation, providing an audit trail.
6. Auditing Group Activations
When a user account activates an eligible Entra ID role or group assignment through Azure PIM, logs are generated that allow for auditing. Within the Insider Threat Matrix, this is tracked as DT106 Microsoft Entra ID Privileged Identity Management Resource Audit.
Within Entra ID > Identity Governance > Groups > Purview Insider Threat Management Investigators, under the Activity section on the left navigation menu, Resource audit presents requests to elevate, successful elevations, and activation expirations.
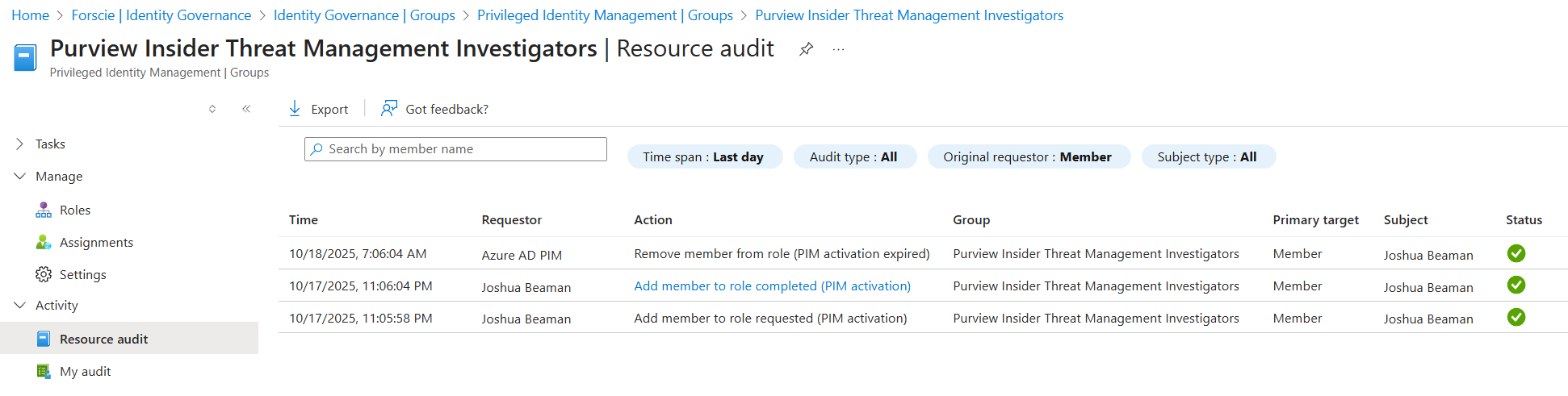
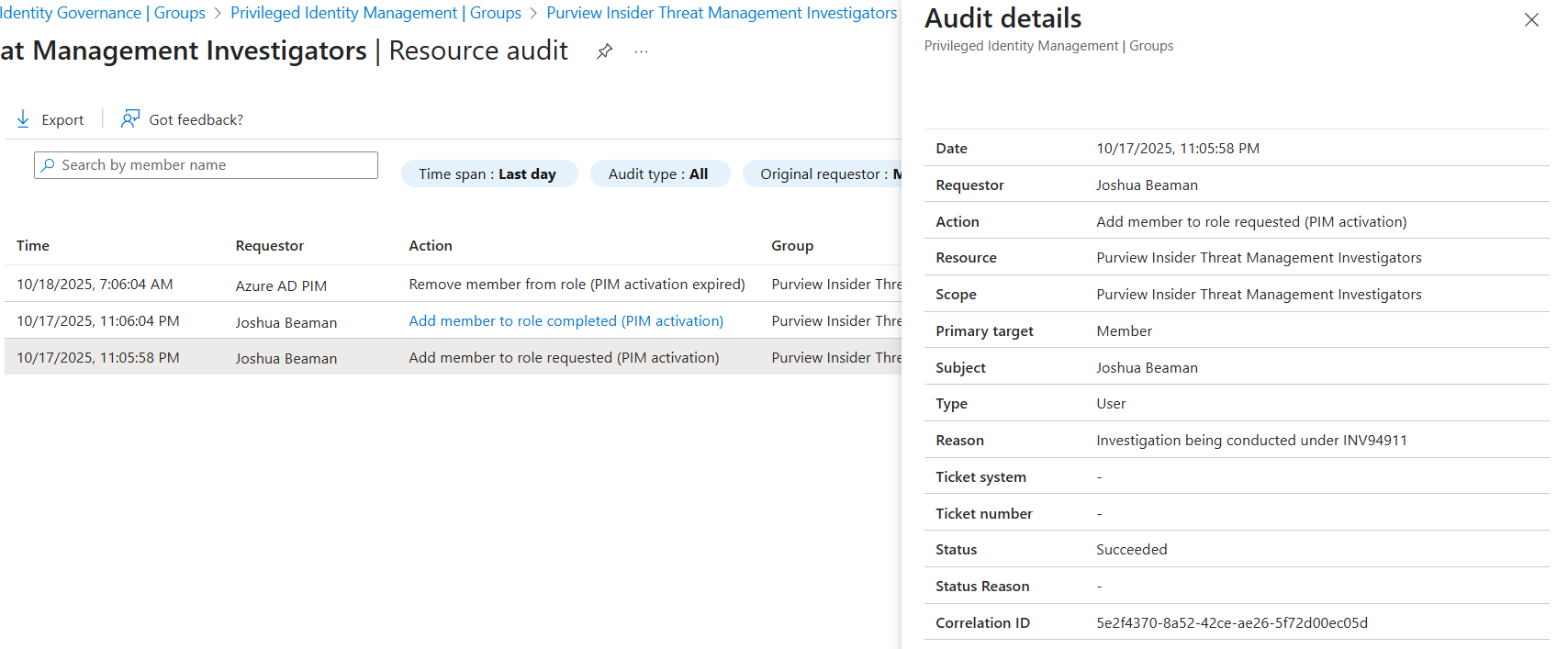
Clicking on a row provides additional information, notably the "Reason" value, which holds the justification the user must provide when activating the group assignment.
7. Conclusion
Microsoft Purview plays a critical role in enabling scoped, auditable, and defensible access to compliance and insider risk management functions within enterprise environments. Its permission model, distinct from tenant-wide Entra ID roles, provides investigators, compliance teams, and legal personnel with the tools they need while minimizing unnecessary exposure to sensitive data.
For organizations seeking to operationalize their insider threat programs with clarity and control, the ability to create custom role groups and implement just-in-time access through Entra PIM offers significant strategic value. These controls not only enforce least privilege and reduce standing access but also generate a detailed audit trail that supports investigation integrity and organizational accountability.
As insider threats increase in both complexity and frequency, capabilities like these form a foundational layer in maintaining trust, ensuring oversight, and empowering defenders to act with confidence.





