1. Investigative Context
In insider threat cases involving data loss, a common assumption is that exfiltration occurs through conventional means: email, cloud uploads, removable media. However, some subjects bypass technical controls altogether by capturing data visually. The native Windows utility Snipping Tool provides one such method: enabling users to screenshot sensitive content directly from screen to file, often without triggering conventional DLP controls.
Whether detected proactively or uncovered during post-incident triage, artifacts from Snipping Tool can serve as evidence of preparation or the act of exfiltration itself, particularly in cases where intellectual property, personal data, or restricted documents are exposed visually.
2. Screenshot Artifact Behavior and Locations
Despite its minimal interface, Snipping Tool exhibits persistent artifact behavior under both default and user-modified settings:
2.1. Primary Screenshot Autosave Location:
When a screenshot is taken using Snipping Tool under its default configuration, the image is automatically saved to the %USERPROFILE%\Pictures\Screenshots\ directory without prompting the user.

2.2. Secondary Silent Screenshot Save Location (when autosave is disabled):
If a user disables the “Automatically save original screenshots” option, they may reasonably assume that screenshots are no longer being stored. However, Snipping Tool continues to retain captured images—redirecting them instead to %USERPROFILE%\AppData\Local\Packages\Microsoft.ScreenSketch_8wekyb3d8bbwe\TempState\Snips\.
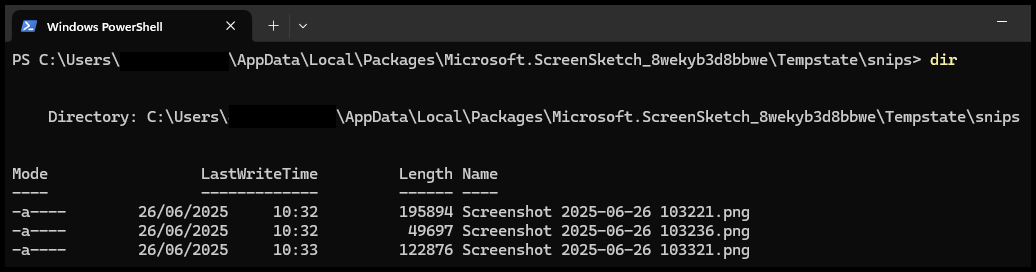
These locations may hold residual screenshots long after their use, and are often overlooked during traditional triage. Investigators should be aware that screenshots may include sensitive data that was never formally stored or transmitted - data that only existed transiently on screen.
3. Screen Recording Artifact Behavior and Locations
3.1. Primary Screen Recording Autosave Location:
When a screen recording is taken using Snipping Tool under its default configuration, the image is automatically saved to the %USERPROFILE%\Videos\Screen Recordings\ directory without prompting the user.

3.2. Secondary Silent Screen Recording Save Location (when autosave is disabled):
If a user disables the “Automatically save original screen recordings” option, they may reasonably assume that screen recordings are no longer being stored. However, Snipping Tool continues to retain captured videos, redirecting them instead to %USERPROFILE%\AppData\Local\Packages\Microsoft.ScreenSketch_8wekyb3d8bbwe\TempState\Recordings\.
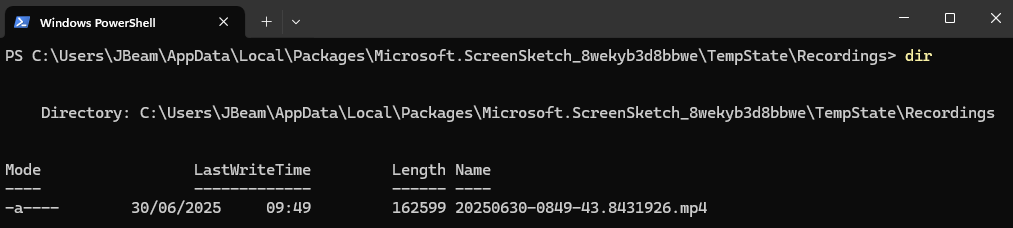
These locations may hold residual recordings long after their use, and are often overlooked during traditional triage. Investigators should be aware that these videos may include sensitive data that was never formally stored or transmitted—data that only existed transiently on screen.
4. Detecting Modified Settings
On Windows 11, Snipping Tool no longer utilizes the Windows registry, instead using a binary registry hive file called settings.dat located at C:\Users\%USERPROFILE%\AppData\Local\Packages\Microsoft.ScreenSketch_8wekyb3d8bbwe\Settings\. To interrogate this file, an appropriate software such as Registry Explorer should be used.
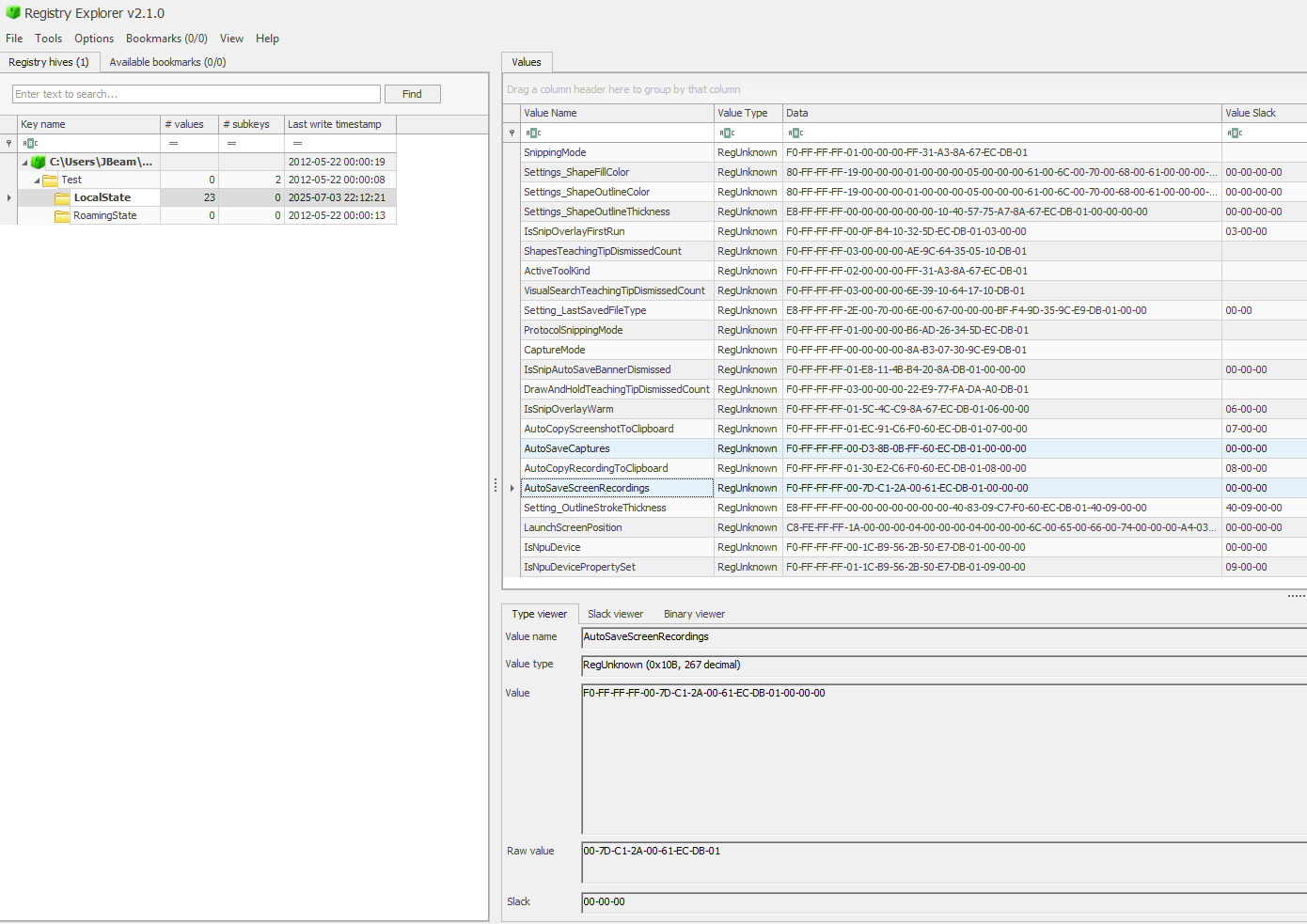
In the above screenshot, two critical rows are highlighted on the right-hand panel, AutoSaveCaptures and AutoSaveScreenRecordings. If the data value begins with F0-FF-FF-FF-00 then the setting is disabled (non-default), if the value begins with F0-FF-FF-FF-01 then it is enabled, which is the default behavior. This can provide evidence that a user account has modified the setting to prevent images or recordings being saved to disk (however in this instance we can use the two fallback artifacts covered above).
Another useful artifact is the last write timestamp, presenting when this key was last modified. The value can be retrieved either by selecting the key in Registry Explorer and looking in the bottom-left corner of the GUI, or by right-clicking a row and selecting ‘Value summary' then pasting the output from the clipboard. An example output is provided below.
Registry file: C:\Users\%USERPROFILE%\AppData\Local\Packages\Microsoft.ScreenSketch_8wekyb3d8bbwe\Settings\settings.dat
Key: LocalState
Last write: 2025-07-03 22:12:21
Value: AutoSaveCaptures (RegUnknown)
Data: F0-FF-FF-FF-00-D3-8B-0B-FF-60-EC-DB-01-00-00-00
Slack: 00-00-005. Relevance to Insider Threat Matrix
These artifacts are directly relevant to two ITM sections in the Prevention & Infringement articles.
PR028 – On-Screen Data Collection
Snipping Tool may be used by subjects to capture regulated data, internal documentation, or third-party information for later exfiltration, printing, or personal reference.IF022 – Data Loss
Screenshots discovered during forensic review may provide direct visual evidence of data compromise—especially when no file transfer activity is recorded.
6. Investigative Use Cases
6.1. Proactive Detection
In environments where sensitive systems are monitored for policy deviation or TempState\Snips may indicate preparatory activity. This is especially relevant where access to data is logged, but actions like screen capture fall outside traditional audit scopes.
6.2. Post-Incident Reconstruction
In data loss investigations where conventional transfer vectors show limited or no activity, Snipping Tool artifacts can close the gap. Investigators may:
Identify what data was viewed and when.
Correlate captures with system focus or user input logs.
Assess intent or motive based on screenshot content and sequence.
Identify autosave file names to correlate with exfiltration activity.
Even in cases where files have been deleted, file system artifacts and shadow volume snapshots may support recovery or timeline reconstruction.
7. Acquisition Guidance
Snipping Tool artifacts are not yet fully covered by standard forensic collection tools. Existing KAPE targets only cover legacy “Snip & Sketch” paths.
A custom .tkape target and PowerShell script have been created to support forensic acquisition across multiple user profiles. This target collects:
Autosaved and fallback screenshots
Metadata for timeline analysis
Retained temp files associated with screen recordings (if applicable)
Download instructions and target usage are available in the Forscie Investigation Kit, available here: forscie-investigation-kit/SnippingTool_Collectors at main · forscie/forscie-investigation-kit
8. Detection Objects
Forscie maintains dedicated detection objects for these behaviors:
These detections can be integrated into SIEM or EDR platforms for early warning or triage enrichment.
9. Behavioral Considerations
The use of visual capture tools often falls outside formal policy boundaries—yet many Acceptable Use Policies fail to explicitly prohibit or define the use of Snipping Tool. In such cases, enforcement becomes a question of context, visibility, and governance maturity. This underscores the importance of explicit, reviewed AUP language and the tracking of
10. Conclusion
Snipping Tool may seem benign, but in the hands of an insider, it offers a low-friction path to data exfiltration, one that is rarely logged, often tolerated, and easily overlooked. Its artifacts offer critical value in both proactive monitoring and retrospective investigation. For defenders, their presence is more than residue, they are signals of intent, opportunity, and sometimes, harm.





