1. Introduction
Insider Threat Matrix Chains (Chains) is an approach that enables information sharing by linking sections and subsections to represent either fictional or non-fictional insider threat incidents. Chains show the trajectory of a
Chains follow the format below, with the ITM framework version as a prefix, and Section or Sub-section IDs delimited by colons:
ITM-V2:MT003:ME024.001:ME011:ME006.001:PR017.003:PR016.001:PR025:PR028.001:IF010.001:AF004:AF0152. The Purpose of ITM Chains
2.1. Insider Intelligence Sharing
Chains provide a way to share information about an insider incident with other parties, without disclosing any confidential information. By populating a Chain with the observed behaviors and events, the Chain string can be shared with other organizations, such as through an ISAC, to help inform other teams what has been observed.
2.2. Pre-Incident Preparation
Chains allows users to view all relevant Preventions and Detections for any objects contained within a Chain. Typically users would need to review each Section or Sub-section to understand the associated PVs/DTs, but using the Prevention and Detection flyouts on the right-hand side, all relevant objects are collated, and hovering over a DT or PV shows the related Sections.
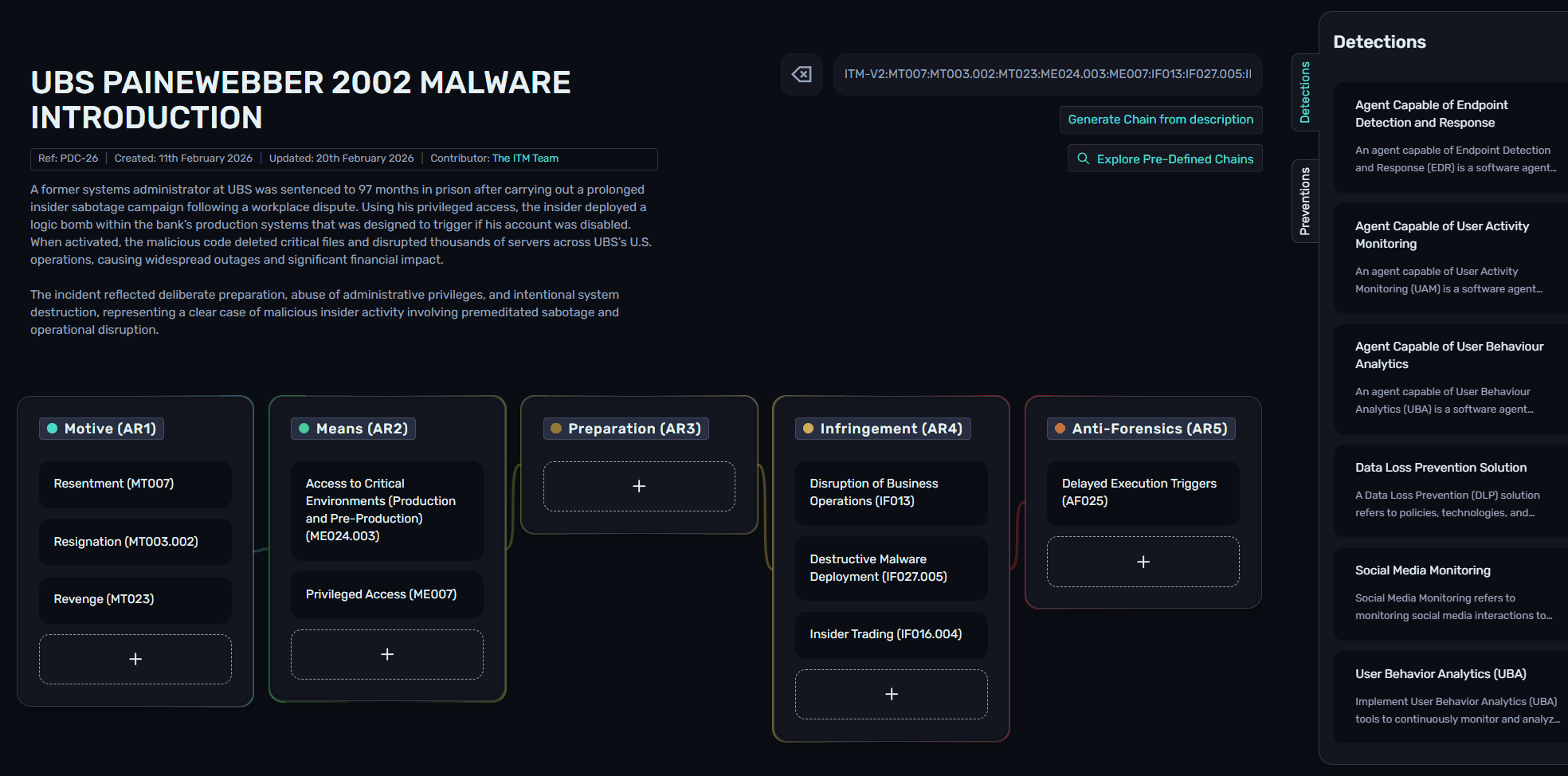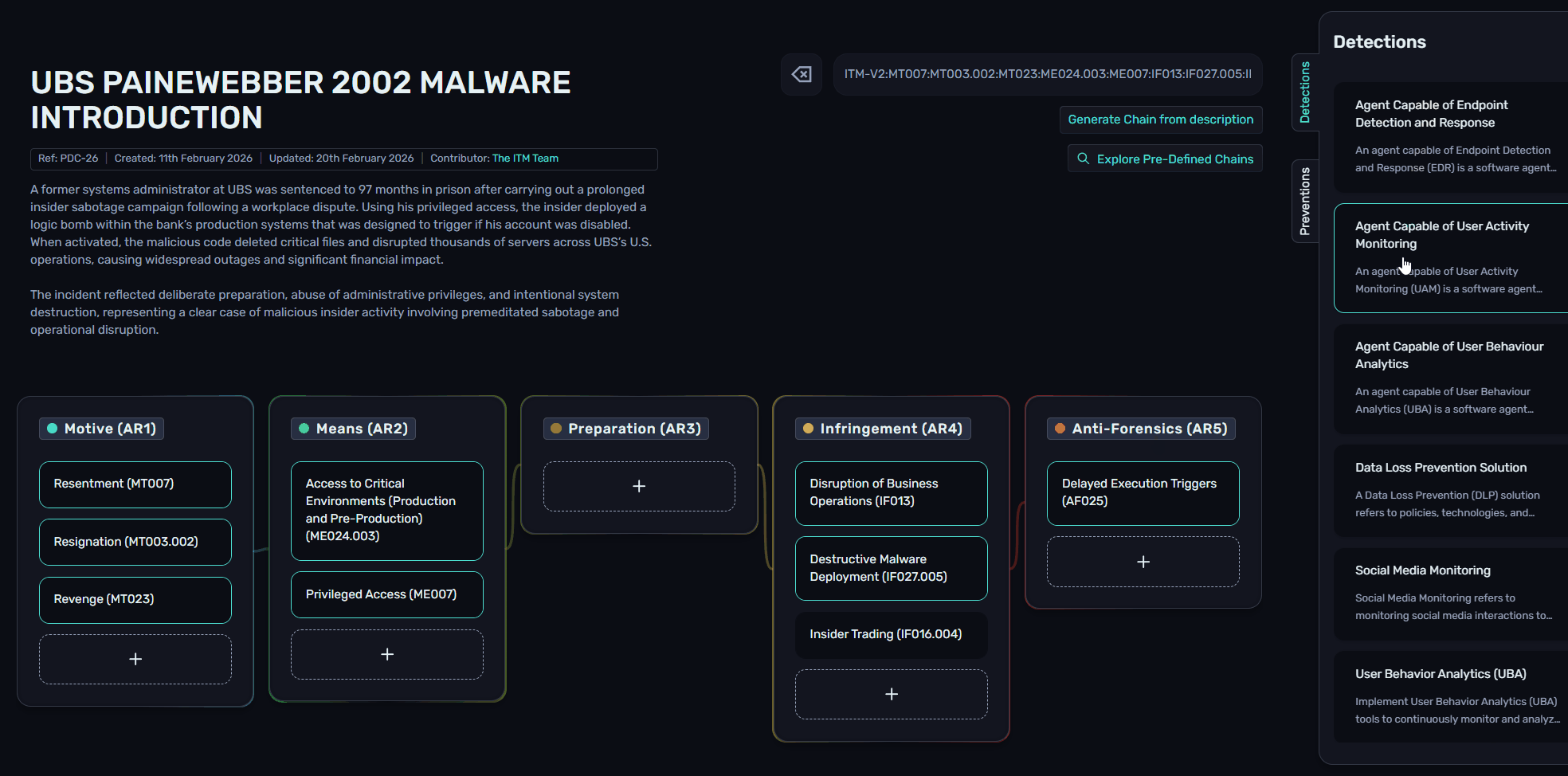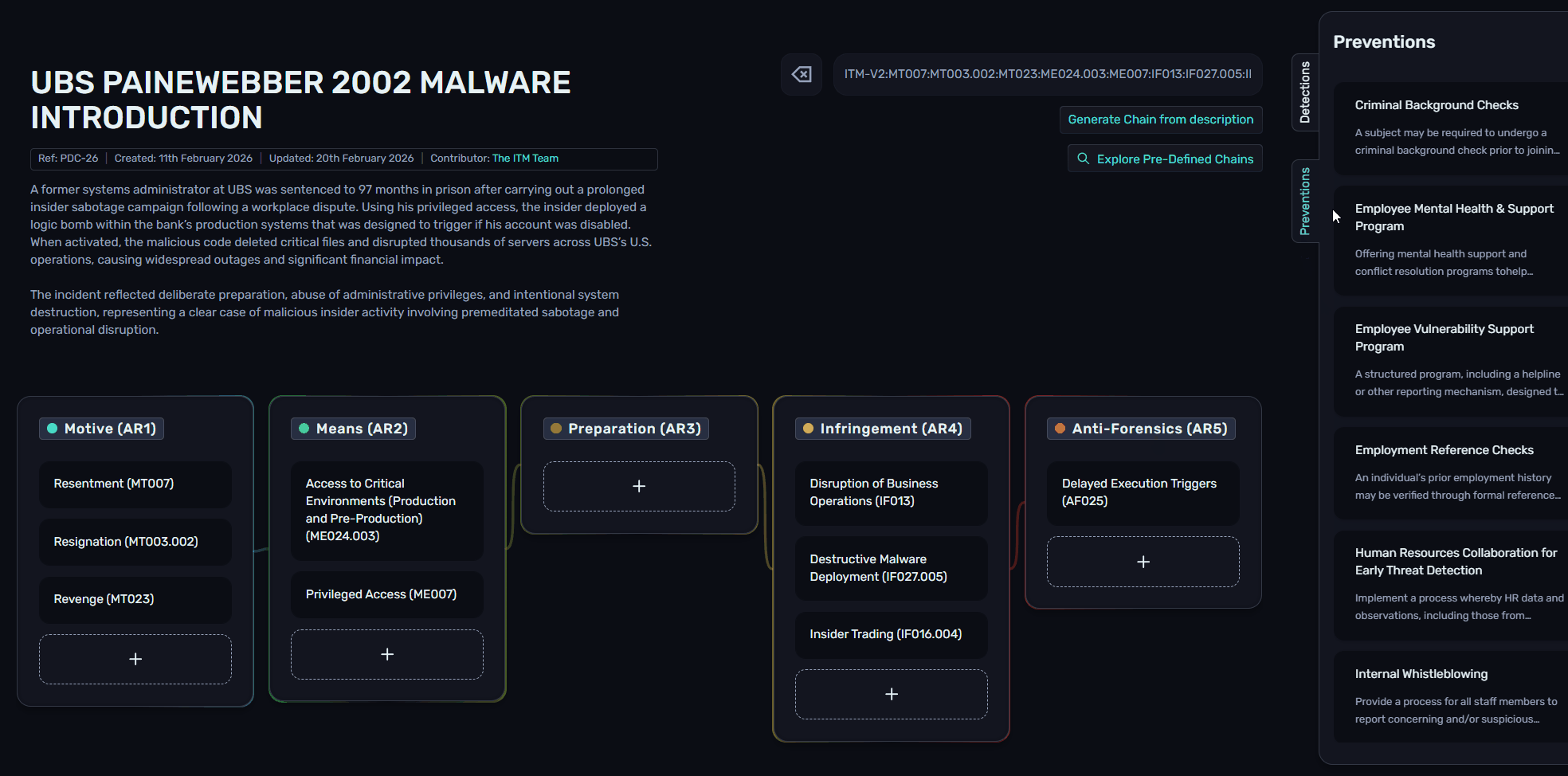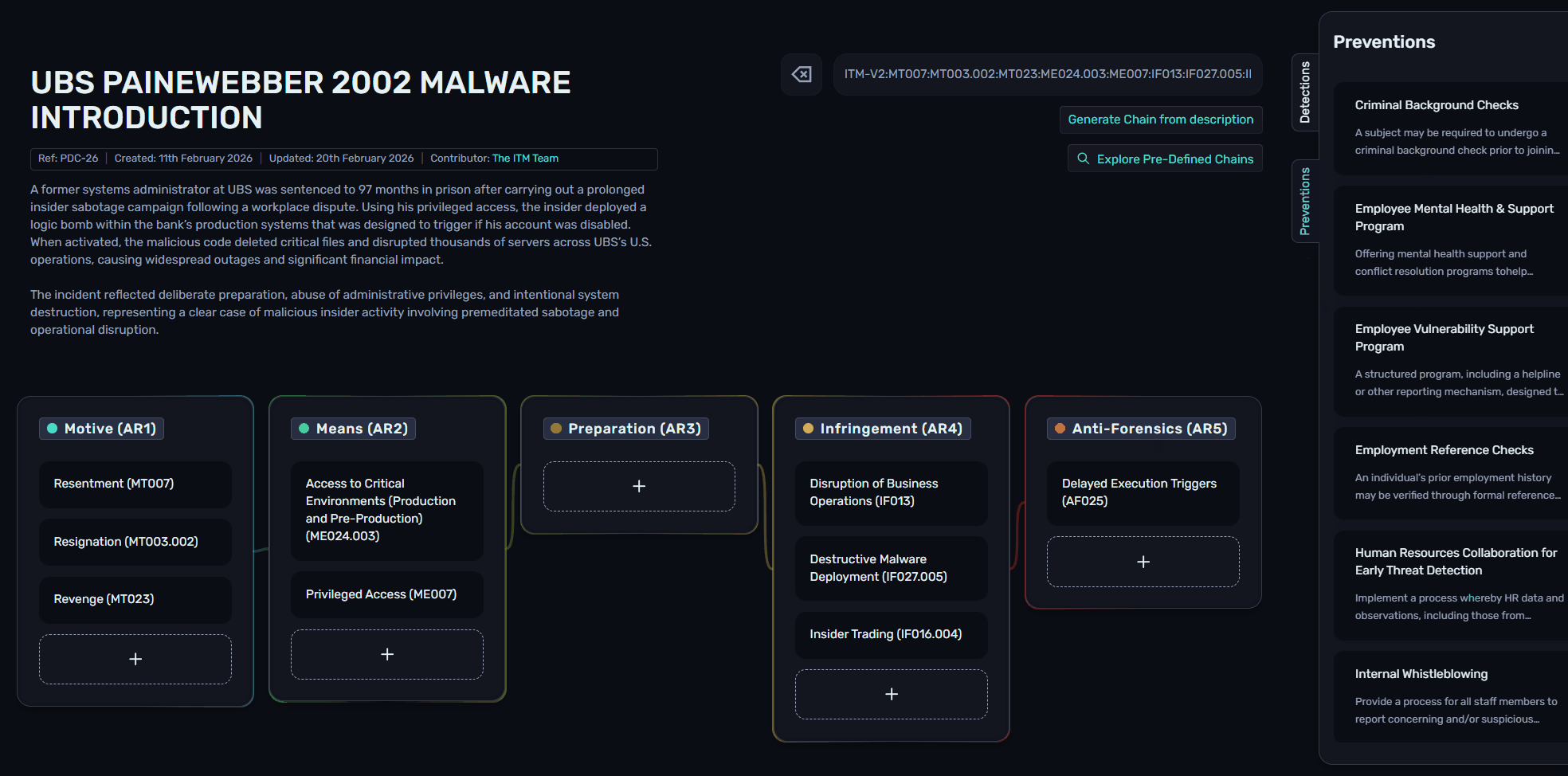
This can be very valuable when viewing PDCs, enabling insider threat practitioners to understand real-world incidents, and how to detect or mitigate them in their own environment.
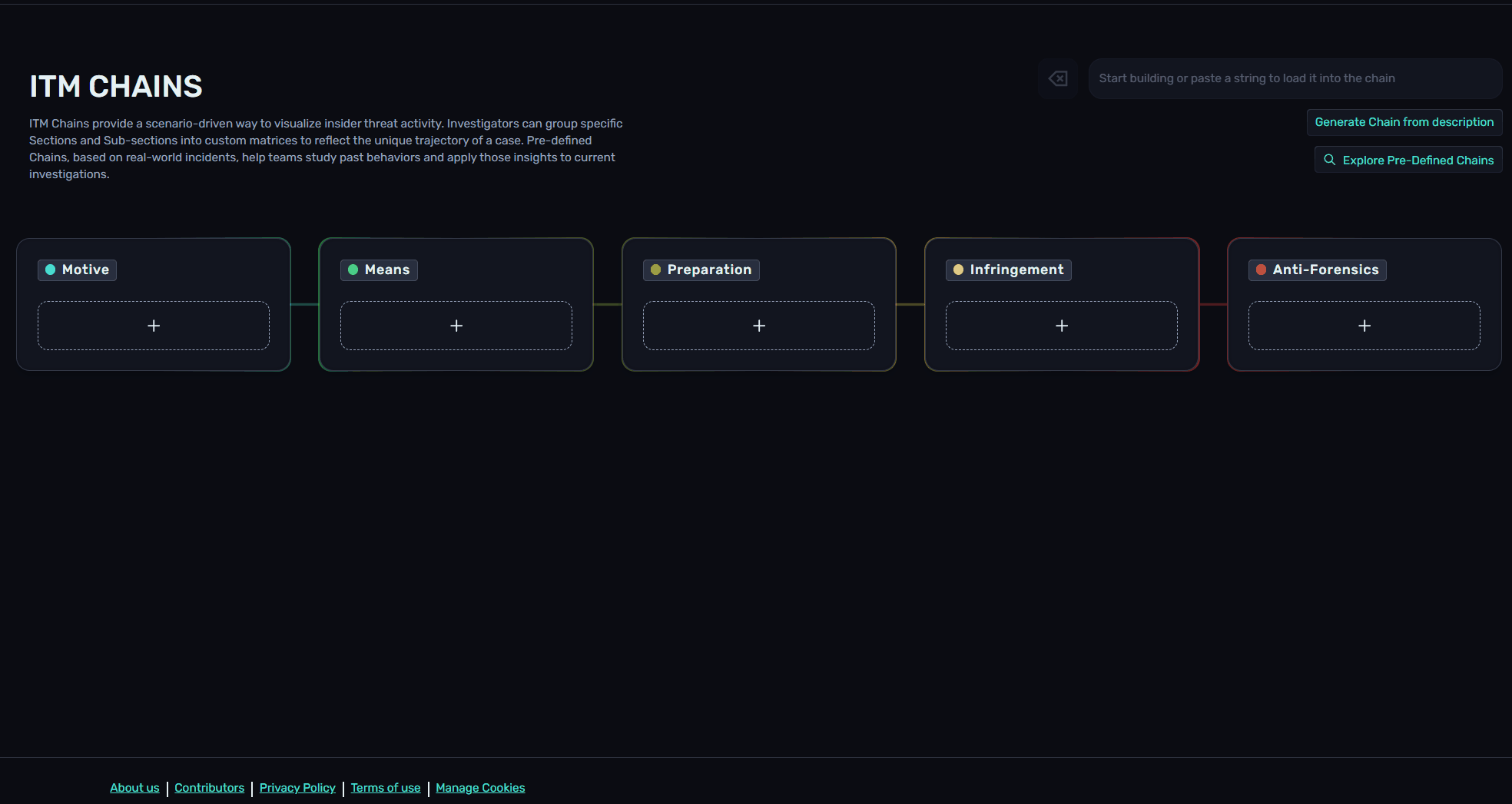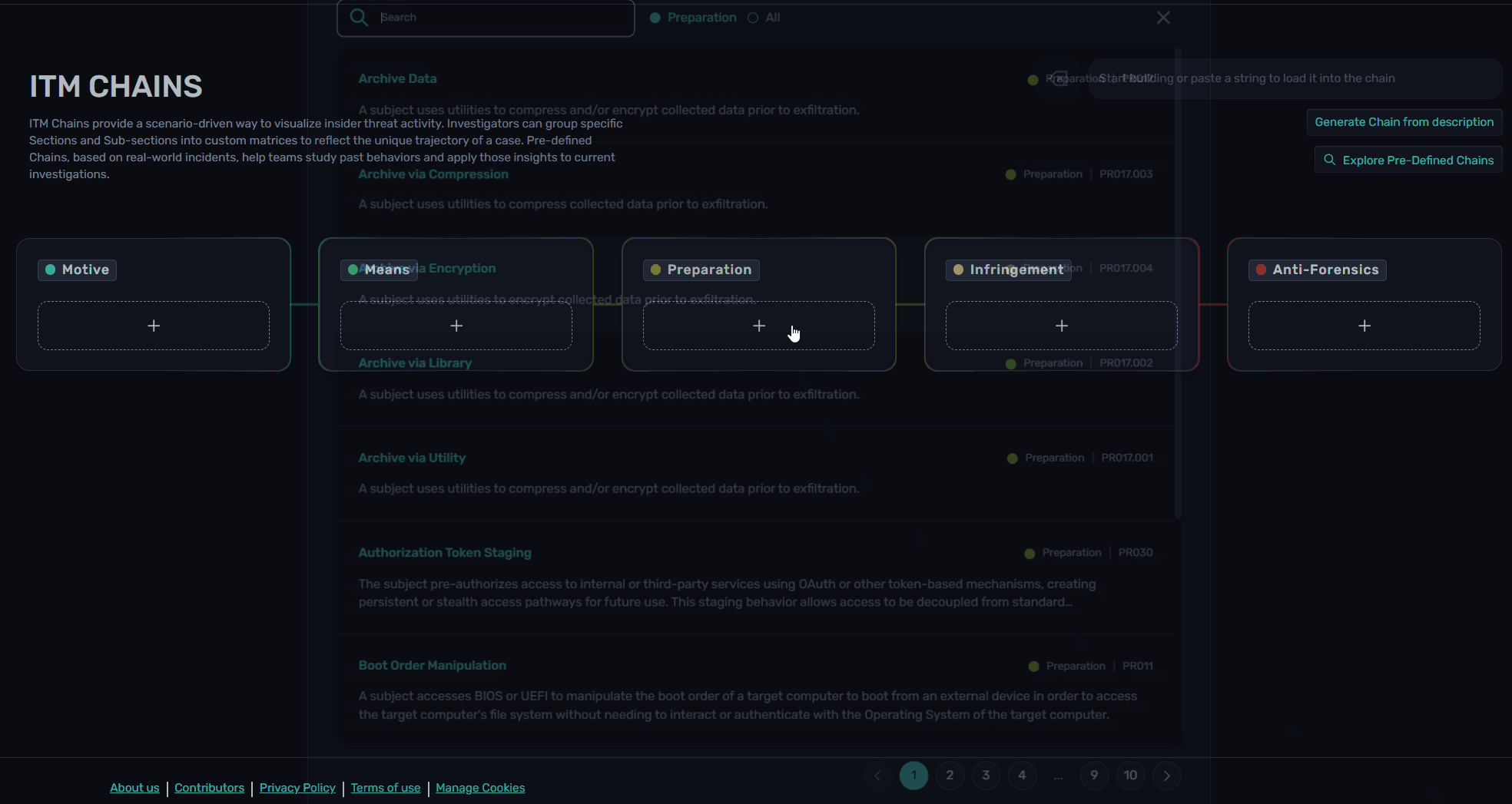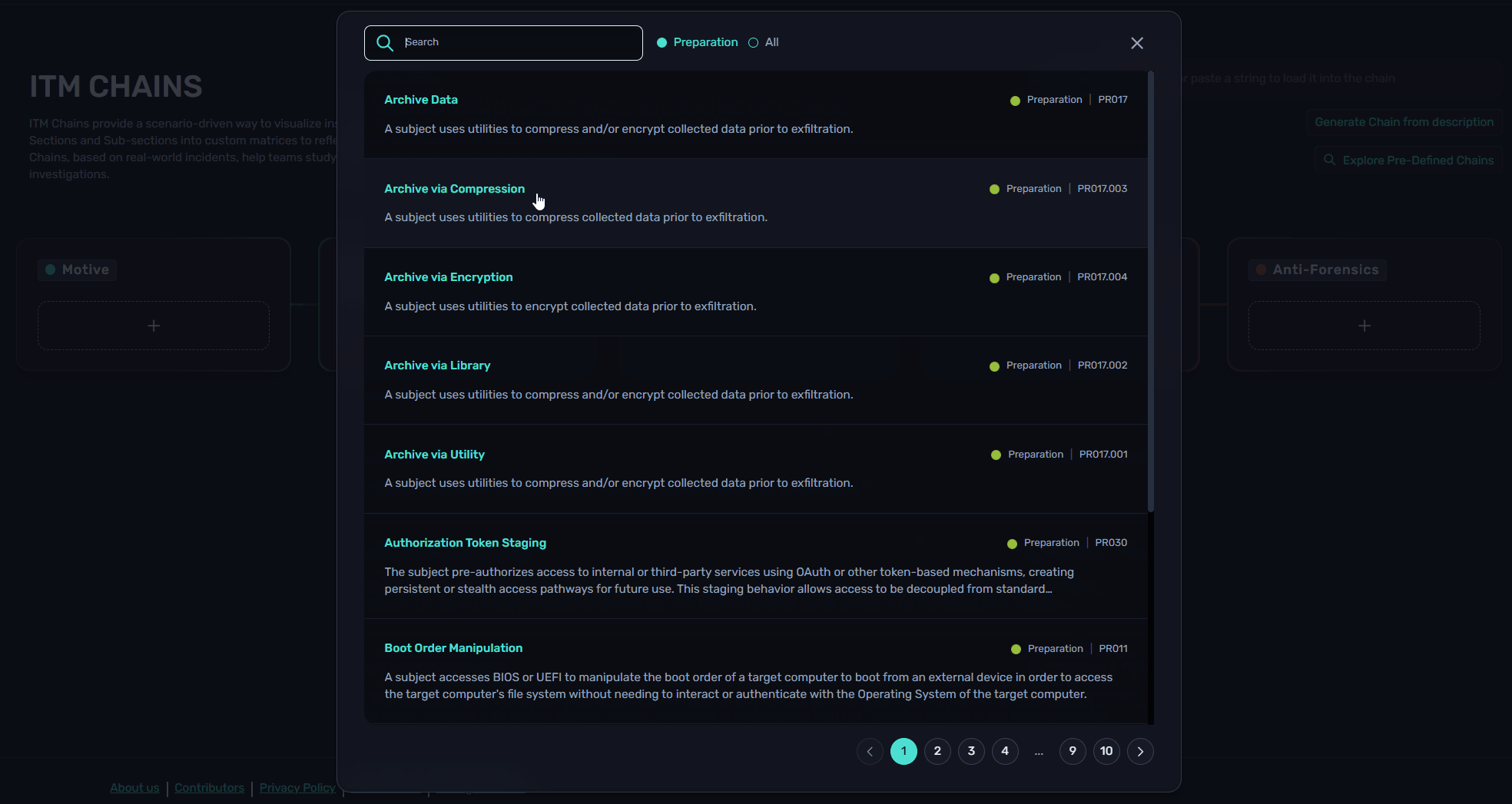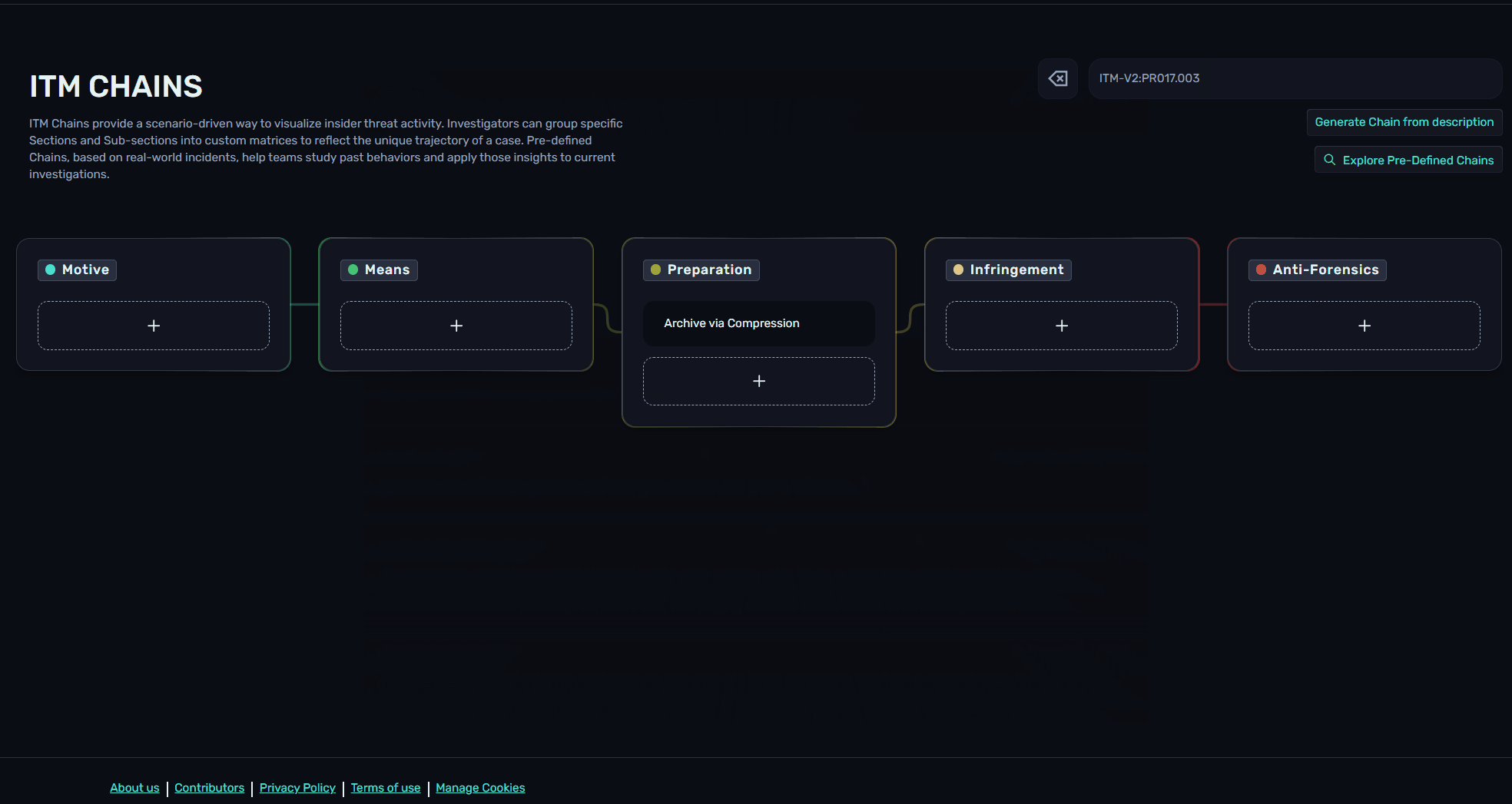
3. Creating Custom Chains
Custom chains can be created from Chain Explorer. Using the "+" button under each Article, users can scroll or search for Sections and Sub-sections.
4. Viewing Pre-Defined Chains
Pre-Defined Chains (PDCs) are published by the ITM Team, and are created internally or through community contributions. These Chains can be viewed by clicking on the "Explore Pre-Defined Chains" button on the right-hand side of Chain Explorer. From here, users can search for keywords or scroll to find a PDC and select it to load the Chain. Filters are available for Documented (real-world) or Simulated (fictional) Chains.
Once loaded, Chain Explorer will display the PDC ID, creation date, updated date, contributor(s), description, and Chain.
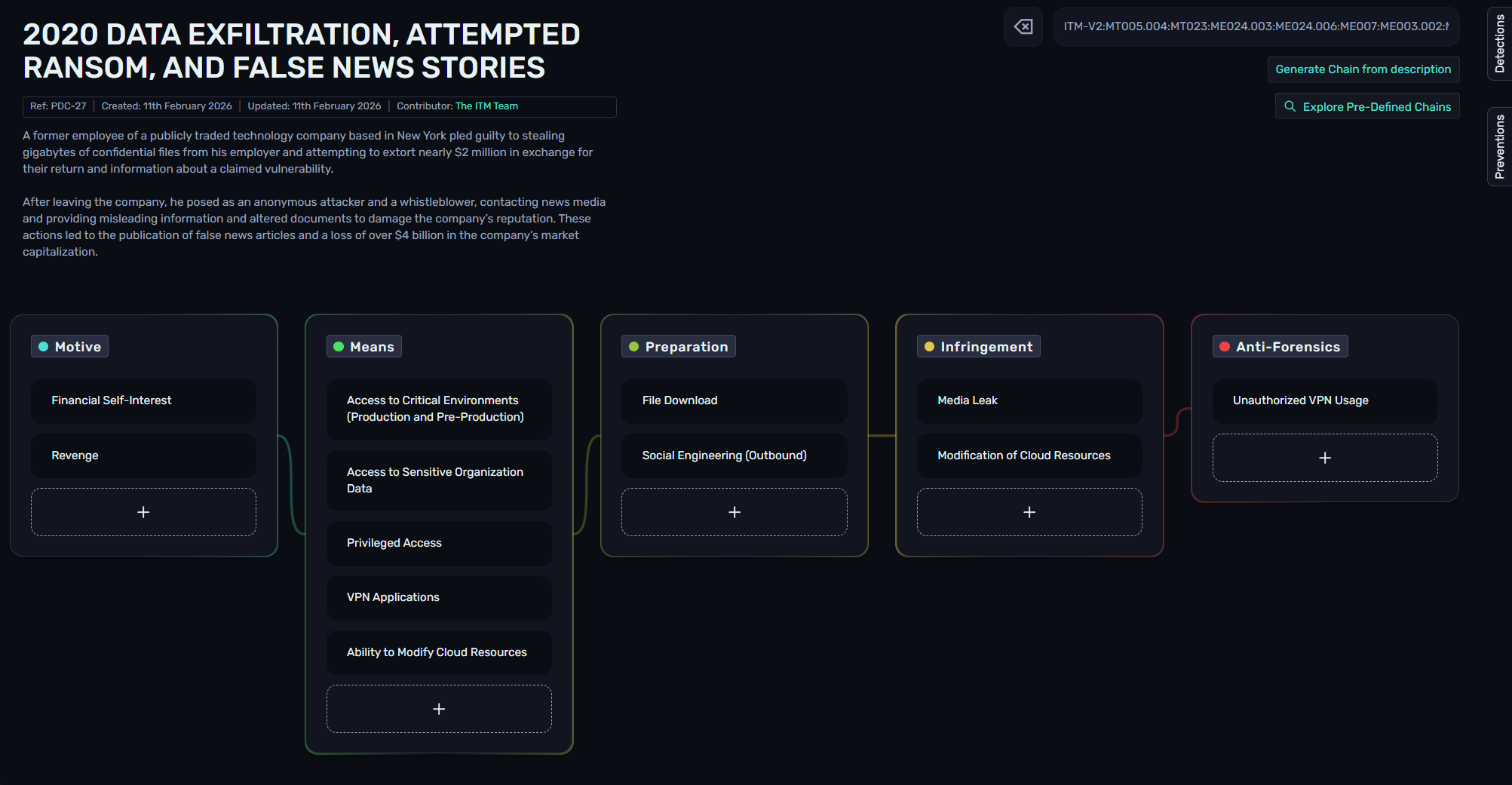
5. Sharing Chains
Chains can easily be shared through two methods; a URL or the Chain string itself. When you have built or loaded the Chain you want to share, copy the full URL from your browser and share this with another party - when viewing the URL, as the Chain string is included, it will load the same page.
Alternatively, copy the Chain string from the right-hand side of the page and send this to another party. They can then paste it into Chain Explorer to load the matrix.
6. Contributing Chains
The Insider Threat Matrix continues to be a collaborative effort within the insider risk community, and Chains are no different. By collectively sharing our knowledge and experiences, we can further our field and help teams better prepare for dealing with insider events.
You can submit Chains through our Contributors page. If you have any general feedback for Chains, you can also let us know from that page.





